Quantum computers cracking BTC
Fact or Fallacy?
2025 saw something strange. Wallets that hadn’t moved since 2011 suddenly woke up. In July, eight wallets controlling $8.6 billion moved simultaneously. In October, a 4,000 BTC wallet worth $442 million stirred for the first time in fourteen years.
Google was announcing quantum breakthroughs. China was making claims about breaking encryption. And these wallets, sitting in address formats everyone knows quantum computers will eventually crack, started transferring funds. The timing looked suspicious. Social media connected the dots: maybe quantum computers had finally done it. Maybe someone cracked Bitcoin’s math.
Some pointed to a $15 billion government seizure as proof. Others whispered about classified NSA programs decades ahead of public research. The story gained momentum because the technology threat is real, the wallet movements were mysterious, and nobody could definitively explain why dormant fortunes suddenly came alive.
So I dug through academic papers, developer forums, quantum computing research, and yes, conspiracy theory corners of the internet. What I found though is probably not the one people want to hear.
The $15 billion seizure happened. But quantum computers had nothing to do with it. U.S. authorities seized approximately 127,271 bitcoins in October 2025 from a Cambodian criminal organization running forced-labor scam compounds. The seizure was traditional law enforcement - tracing fraud proceeds, international cooperation, blockchain forensics. Not cryptographic cracking.
But the backstory involves exactly the kind of vulnerability people confuse with quantum threats. Those bitcoins traced back to a Chinese mining pool called Lubian, which used a random number generator called Mersenne Twister MT19937 for wallet key generation. It works fine for video game randomness or running simulations. It’s catastrophically bad for generating cryptographic keys. The “randomness” followed predictable patterns. With ordinary computers, attackers could work backward and figure out the private keys.
In December 2020, over 130,000 BTC drained from Lubian-linked wallets in a matter of hours. Researchers later connected this to the “Milk Sad” vulnerability - the same weak randomness flaw found in early versions of Trust Wallet and Libbitcoin Explorer. Whether it was an external hack or an inside job remains unclear. Either way, the coins eventually ended up with criminals, and that’s who the government seized them from.
No quantum physics needed. Just exploiting sloppy software from Bitcoin’s early days. Calling it a “quantum breakthrough” is like calling a locksmith picking a cheap lock proof that teleportation exists.
But that still doesn’t explain why all those ancient wallets moved. To understand that, you need to understand what quantum computers actually threaten in Bitcoin.
Bitcoin’s security rests on two different types of math. One is basically quantum-proof. The other isn’t. The difference matters.
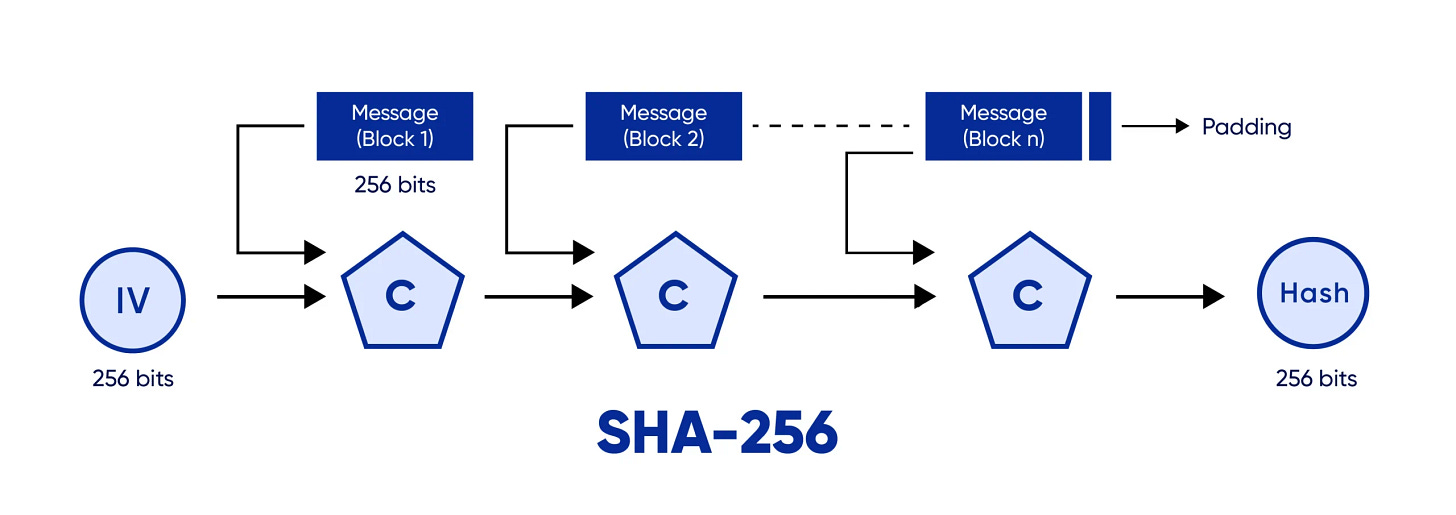
First, there’s SHA-256, the hash function. This is what miners do when they mine Bitcoin. You put data in, you get a unique 256-bit number out. You can’t reverse it. Think of mixing paint—once you’ve blended red and blue to make purple, you can’t separate them back into pure colors. Quantum computers can speed up attacks on hash functions using something called Grover’s algorithm, but only by about a factor of two. That sounds impressive until you realize it just means we’d eventually need to use longer hashes. SHA-256 remains secure against quantum attacks for any reasonable planning horizon.
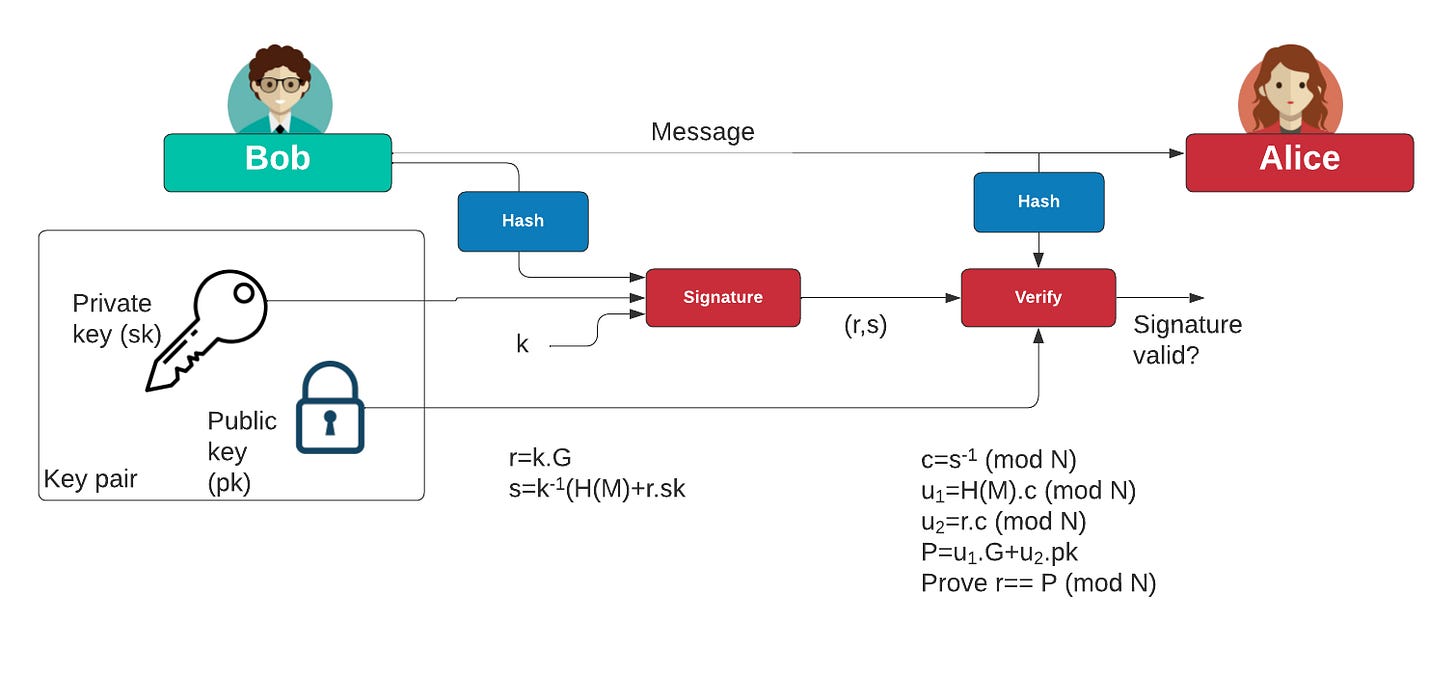
Then there’s ECDSA, the signature system. This is what actually protects your coins. Every Bitcoin address has a public key and a private key. The public key is like your account number. The private key is like your password. The public key is derived from the private key using elliptic curve mathematics—easy to go forward from private to public, essentially impossible to go backward from public to private. At least with normal computers.
With quantum computers running Shor’s algorithm, that “essentially impossible” becomes “doable.” This is the vulnerability.
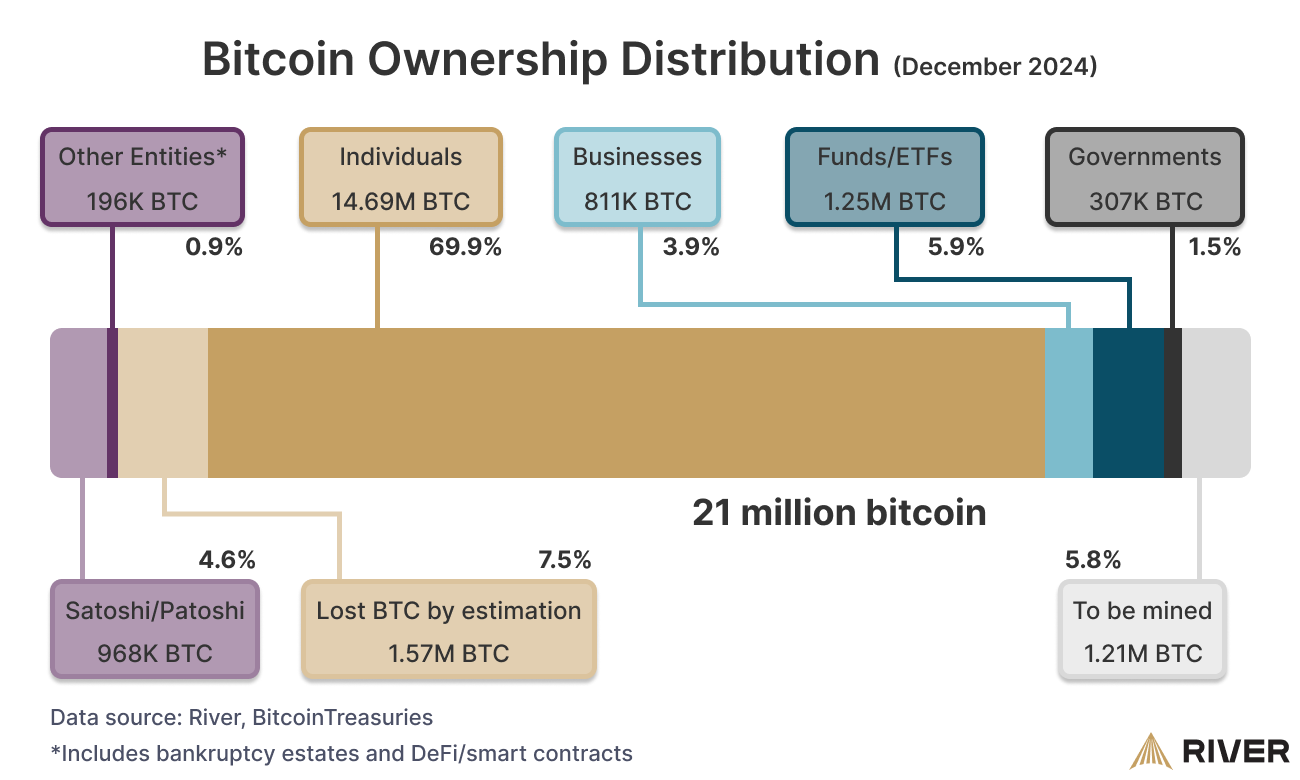
But not all Bitcoin addresses are equally exposed. Pay-to-Public-Key addresses, used heavily from 2009 to 2011, put your entire public key on the blockchain the moment you receive coins. It sits there permanently. Anyone can see it. Satoshi Nakamoto’s estimated 1.1 million BTC lives in these addresses. Newer address formats like Pay-to-Public-Key-Hash and SegWit are smarter—they only reveal your public key when you spend coins. Until then, only a hash of your public key is visible, and quantum computers can’t crack hash functions efficiently.
Here’s the catch though. Once you spend from a P2PKH or SegWit address, your public key is exposed forever. Move your coins somewhere else and you’re safe again. But that old address? Now vulnerable.
Rough estimates suggest 25-30% of all Bitcoin—somewhere between 4 and 7 million BTC worth over $500 billion—sits in addresses with exposed public keys right now. That’s the quantum treasure chest everyone’s worried about.
So back to October. Those ancient wallets that suddenly moved? They were doing exactly what security experts recommend: migrating from permanently exposed address formats to temporarily safer ones. The pattern was consistent. Wallets didn’t drain completely. They moved portions to fresh SegWit addresses that had never made outgoing transactions. The 4,000 BTC wallet only moved 150 BTC initially. The $8.6 billion whale split funds across multiple modern SegWit addresses.
This is what people call “quantum housekeeping.” Moving coins from P2PK addresses where your public key has been visible since 2011 to unused addresses where it’s still hidden. It buys time. Not permanent safety, but an upgrade.
Several things converged in October. Bitcoin hit all-time highs above $126,000. If you bought in 2011 at $10 per coin, you’re now sitting on a fortune. Time to take security seriously. Some of these ancient wallets also received spam messages—blockchain notices claiming legal ownership of the coins. Almost certainly fake, but they spooked owners into action. Ledger’s CTO confirmed the $8.6 billion movement was triggered by these spam messages.
Then there were the institutional warnings. BlackRock added quantum computing warnings to its Bitcoin Trust filing back in May. The Federal Reserve published a report about “harvest now, decrypt later” threats—the idea that adversaries can download the blockchain today and wait for quantum computers to crack it tomorrow. When the world’s largest asset manager and the central bank both flag quantum risk, people with nine-figure Bitcoin holdings pay attention.
What we didn’t see: evidence of actual quantum breaches. No sudden complete wallet drains. No pattern suggesting attackers testing capabilities. Just cautious, partial movements to better security formats. Exactly what you’d do if you were sitting on generational wealth and genuinely worried about future threats.
Which brings us to the real question: where does quantum computing actually stand?
Current state of the art quantum computers run about 150 qubits. Google’s Willow has 105. IBM’s systems reach 156. China’s Zuchongzhi 3.0 has 105. What’s needed to break Bitcoin’s ECDSA signatures? Conservative estimates say 13 million physical qubits. Realistic estimates say 317 million physical qubits.
The gap is somewhere between 80,000 times and 2 million times what currently exists.
This isn’t “maybe classified programs are ahead” territory. This is “the laws of physics haven’t been suspended” territory. Why such enormous numbers? Error rates. Current quantum computers are noisy. Qubits make mistakes constantly. To build one reliable “logical qubit” that does useful calculations, you need hundreds or thousands of error-prone physical qubits working together to catch and correct each other’s errors. It’s like needing 500 unreliable cars to build one reliable transportation system through redundancy.
Breaking Bitcoin requires about 2,330 logical qubits running Shor’s algorithm. Multiply by the error-correction overhead and you’re in the millions of physical qubits. China’s recent “breakthrough” that made headlines? They cracked 22-bit RSA encryption. Bitcoin uses 256-bit ECDSA. The computational difficulty doesn’t scale linearly. Each additional bit roughly doubles the work. The gap between 22 bits and 256 bits is approximately 2 to the power of 234 times harder. That’s a number with 70 digits.
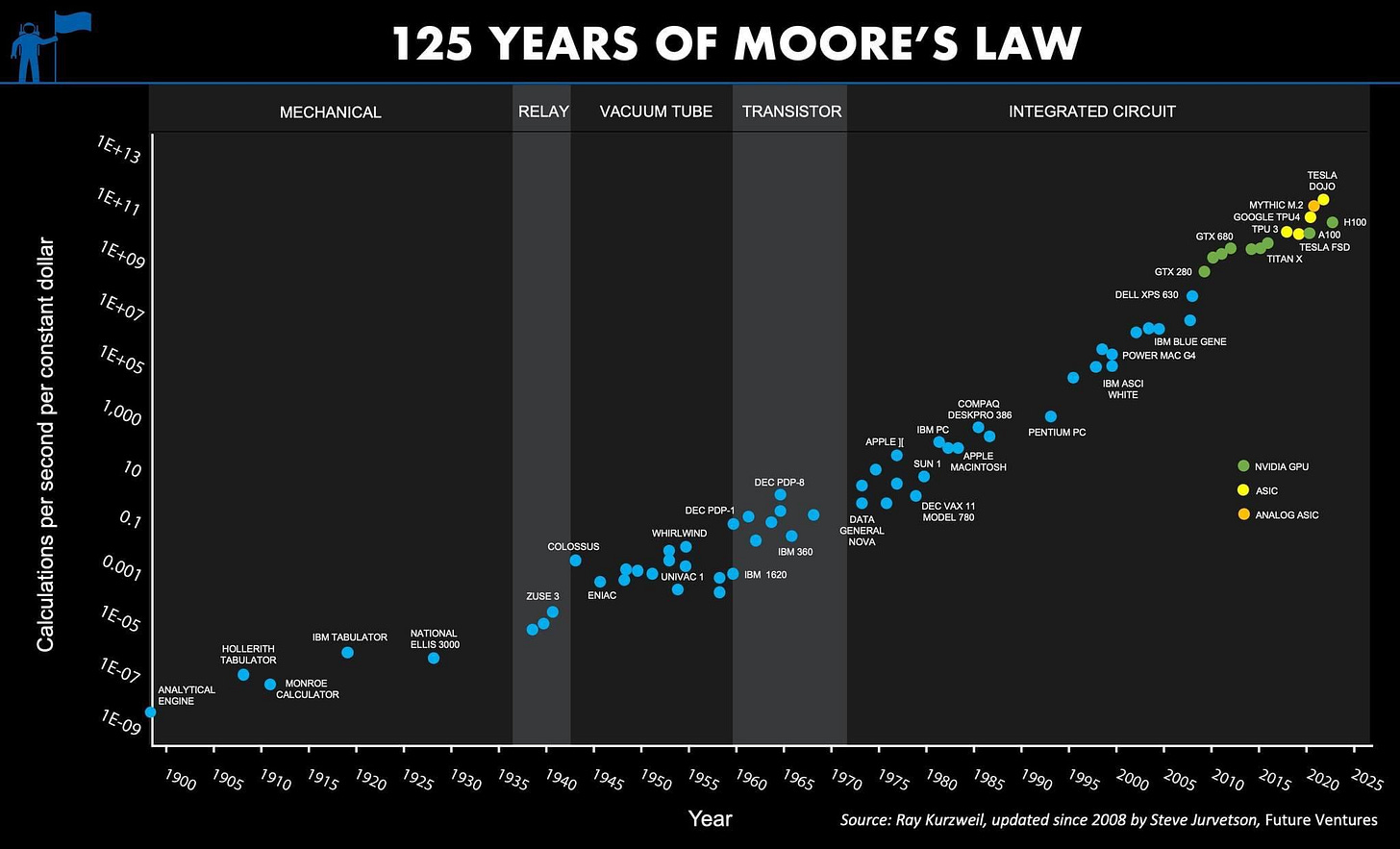
People like to invoke Moore’s Law here. Classical computing power doubled every 18-24 months for decades. If quantum computing followed the same curve, we could calculate when quantum computers become dangerous. Starting from 150 qubits today, needing 13 million, doubling every 18 months... you’d hit the target around 2049.
Except quantum computing doesn’t follow Moore’s Law. Not even close. Classical computing scaled predictably because the challenge was pure engineering. Make transistors smaller. Pack more onto chips. Improve manufacturing. Physics was cooperative. You could brute-force progress with money and incremental refinements.
Quantum computing faces fundamental physics problems. Qubits are fragile. They lose their quantum state from the tiniest environmental interference. Error rates haven’t improved on the same exponential curve as qubit counts. Different approaches are competing—superconducting, trapped ion, photonic, topological—with no clear winner. Scaling isn’t just “build more qubits.” It’s “build more qubits that can all talk to each other reliably while staying cold enough and isolated enough to maintain quantum states.”
Progress has been sporadic. IBM went from 5 qubits in 2016 to 127 qubits in 2021 to 433 qubits in 2022 to 1,121 qubits in 2023. Impressive. But they’re still millions away from breaking cryptography, and error rates remain stubbornly high.
Recent developments show both progress and limitations. In May 2025, Google researcher Craig Gidney showed that cracking RSA might require 20 times fewer resources than previously thought. Not a hardware breakthrough—an algorithmic improvement. Similar gains might apply to ECDSA. Might. December 2024 saw Google’s Willow chip achieve something genuinely important in error correction. For the first time, adding more qubits reduced errors instead of increasing them. This matters for future scaling. But Willow has 105 qubits. We’re still at base camp.
IBM announced plans for fault-tolerant quantum systems by 2029. Théau Peronnin, CEO of Alice & Bob—Nvidia’s quantum partner—estimated quantum computers could crack Bitcoin “a few years after 2030.” These are targets, not guarantees. Expert timelines range from Adam Back’s conservative 20-40 years to Scott Aaronson’s “live possibility by 2028,” though Aaronson is careful to emphasize possibility rather than certainty.
What this means practically: probably safe for the next 5 years. Almost certainly safe for 10. Beyond that, uncertainty compounds rapidly.
The Federal Reserve’s October 2025 warning about “harvest now, decrypt later” is the concerning part. Adversaries can download the entire Bitcoin blockchain today. It’s public data. They can store every transaction with exposed public keys and wait. When quantum computers become powerful enough—whenever that is—they’ll crack those stored records and steal coins. This threat is active now, not because quantum computers work today, but because data collected today will be vulnerable tomorrow.
Every quantum conspiracy theory includes the NSA caveat. What if they’re decades ahead in secret? We know from Edward Snowden’s leaks that the NSA had a classified program called “Penetrating Hard Targets” with an $80 million budget specifically for building quantum computers to break encryption. But even those leaked documents from 2011-2014 showed the NSA struggling with basic problems. One document described their goal as factoring numbers “up to four.” Not four-digit numbers. The number four.
Several reasons suggest classified programs aren’t wildly ahead. Both Google and IBM’s quantum computers use transmon qubits—a design invented under NSA funding at Yale in the early 2000s. If the NSA had dramatically better technology, they probably wouldn’t have sponsored development of the building blocks everyone else now uses. Quantum computing isn’t just engineering you can throw money at. You can’t compress timelines arbitrarily. Qubits require near-absolute-zero temperatures, extreme isolation, precise control. These are fundamental physics challenges that don’t care about classification levels.
There’s also the recruitment problem. Quantum computing requires world-class physicists and engineers. Most want to publish papers, win prizes, advance science publicly. Classified programs struggle to recruit and retain top talent compared to Google, IBM, or MIT. Historical precedent shows the NSA was ahead on some cryptographic techniques—differential cryptanalysis was classified before going public—but the gap was years, not decades. And that was pure mathematics, easier to keep secret than massive hardware projects.
Could the NSA be 5-10 years ahead? Possibly. Could they be 20+ years ahead with working quantum computers that crack Bitcoin? Only if physics works differently in Maryland.
If quantum Bitcoin cracking were possible today, behavior would look different. Wallets would drain completely and instantly. Billions would vanish overnight, not tens of millions moving cautiously to new addresses. The theft would be obvious because the goal would be maximizing extraction before discovery.
Instead we’re seeing legitimate owners nervously upgrading security while they still can. Which points to the actual near-term risk.
The most likely quantum threat to Bitcoin in the next few years isn’t Shor’s algorithm. It’s panic. Markets run on confidence. Bitcoin’s value proposition rests on mathematical security—the belief that nobody can steal your coins if you hold the keys. Introduce doubt about that premise and the price can collapse long before the cryptography breaks.
We saw this in 2017. A fake 4chan post claimed Ethereum founder Vitalik Buterin had died. Billions in market value evaporated in minutes. The post was obviously false, but in the moments before verification, fear moved faster than truth. Yoon Auh, founder of post-quantum cryptography company BOLTS, warned about exactly this scenario with quantum. “Imagine hearing someone say elliptic curve cryptography can be broken now, maybe not instantly, but soon. Everyone would rush for the exit. The system would trip over itself.”
In April 2025, a single tweet from Donald Trump threatening 100% tariffs on Chinese imports triggered $19 billion in crypto liquidations. Bitcoin briefly plunged below $102,000. That was just trade policy. A credible quantum scare could be worse.
The danger compounds because quantum progress is legitimately hard to assess. When Google announces a breakthrough, is it incremental progress or a paradigm shift? Most Bitcoin holders can’t evaluate technical details. They rely on headlines and expert interpretation. A well-timed misinformation campaign could destabilize markets even if the underlying threat remains years away. All it takes is a fake demonstration, a misinterpreted research paper, or an ambiguous government statement about quantum capabilities.
This is why institutional players take the threat seriously now. BlackRock’s quantum warning in its Bitcoin Trust filing isn’t because danger is imminent. It’s fiduciary responsibility requiring acknowledgment of risks even when distant. But those warnings, meant to show prudence, can fuel the panic they’re trying to prevent.
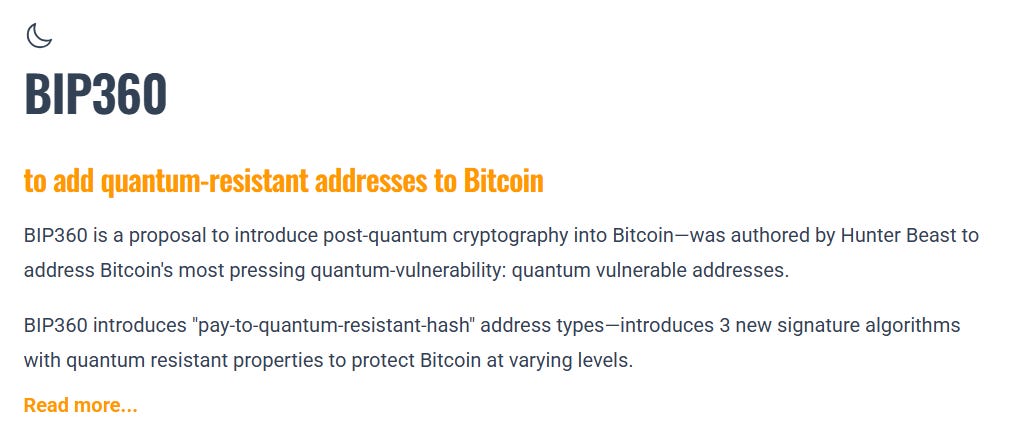
The cryptographic solutions exist. NIST standardized post-quantum algorithms. Bitcoin Improvement Proposal 360 proposes migration paths. The technology isn’t the bottleneck. The governance is.
Bitcoin has no CEO, no board, no update mechanism beyond rough consensus among thousands of independent operators. This decentralization is its greatest strength and its quantum weakness. Implementing quantum-resistant signatures requires a hard fork or extensive soft fork—changes affecting everyone. The Bitcoin community spent years arguing over block size limits. Quantum security is infinitely more complex.
A Chaincode Labs study estimated full migration would take approximately seven years. The University of Kent calculated it could require 76-305 days of network downtime. Months where Bitcoin might be essentially frozen while upgrading. Then there’s the philosophical problem of coins that can’t migrate.
Satoshi’s 1.1 million BTC sits in P2PK addresses with exposed public keys. Moving those coins requires the private keys Satoshi apparently doesn’t plan to use. Same for perhaps another 600,000 BTC in provably lost wallets from Bitcoin’s early days. If these coins can’t migrate to quantum-safe addresses, they become permanent bounties. The first entity to build a cryptographically-relevant quantum computer could instantly claim $150+ billion in abandoned Bitcoin.
Some propose freezing these coins—making them unspendable through protocol change. This would protect the network from the destabilizing shock of massive theft. But it violates Bitcoin’s core principle: nobody can stop you from spending your coins if you have the keys. Others argue let quantum thieves take lost coins. It’s a one-time inflation event, but it respects that Bitcoin’s rules allowed anyone with valid keys to move coins—even if those keys were derived through quantum computing rather than mining or purchase.
Jameson Lopp wrote an essay titled “Against Quantum Recovery of Bitcoin” arguing for freezing vulnerable coins. Paolo Ardoino, CTO of Tether, countered that recovering lost coins might be preferable to permanent loss. These debates aren’t abstract philosophy. They’ll determine whether Bitcoin can implement quantum security without tearing the community apart.
If quantum computers advance faster than expected and Bitcoin’s governance moves slower than expected, the window for orderly transition closes. The result would be either a rushed, contentious hard fork under crisis conditions or a slow-motion disaster as the quantum threat becomes undeniable but consensus remains elusive.
Did quantum computers crack Bitcoin in October 2025? I don’t think so. The gap between current capabilities and cryptographic relevance remains vast - probably a decade, possibly longer. What happened was simpler: wealthy early adopters, spooked by institutional warnings and legitimate long-term concerns, quietly moved coins from vulnerable address formats to safer ones while prices peaked.
You don’t need to understand quantum physics to protect yourself. Use modern wallet software that doesn’t reuse addresses. Don’t leave coins in addresses you’ve already spent from. If holding long-term, move to fresh addresses every few years. Watch for Bitcoin community announcements about quantum-safe upgrades. Don’t panic-sell based on breathless headlines about quantum “breakthroughs.”
Short term, the highest risk isn’t quantum anything. It’s traditional hacks, exchange failures, phishing, lost keys. Focus on basic security first.
Smart money secures itself before a crisis, not during. That’s what we saw in October. Those ancient wallets woke up for the most boring reason possible - not because quantum computers cracked them, but because their owners finally got nervous enough to act.
Turns out the answer wasn’t physics. It was psychology.










It's comforting to know that there is no investment that you can stop worrying about. More evidence here that one can fake their way through liberal arts classes but STEM rises to a whole
other level. I'm more likely to buy a nice property on a canal in Amsterdam...paid for with very special tulip bulbs...than comprehend the nuts and bolts of this post. I got what was charitably called a Gentlemen's "C" in my brief brush with anything mathematical in school.
I'm wondering what Frankfort, The City, Belgium and Euroclear will look like when the Russians decide to finally discipline the Euro-pirates with large amounts of carefully deposited Oreshniks?
"because that's where they keep the money...."
Willie Sutton's response when asked why he robs banks.
Outstanding breakdown of the actual quantum threat timeline versus the perception risk. The insight about panic being the realvulnerability before cryptographic failure is spot-on. When institutions like BlackRock flag quantum risks in filings while holders sit on exposed P2PK addresses, we're watching a slow-motion game of musical chairs where the music hasn't stopped yet but everyone's nervously eyeing the exits. Your point about 'quantum housekeeping' reframes those October movements perfectly - not evidence of breakthrough, but rational actors hedging against future uncertainty.The seven-year migration timeline you mentioned is the critical bottleneck nobody talks about enough.